Security Management
Most Secure Enterprise Grade ERP
ERP security management is critical to the success of any organization. Every company that deploys an ERP system must have a comprehensive security plan in place to protect its sensitive data. Security threats come in many forms, so it is essential to be prepared for them.
One common threat is unauthorized access to data. Hackers could gain access to your system by exploiting software vulnerabilities or guessing your passwords. They can then steal or damage your data, costing you time and money.
SIX ERP Handles most security-related tasks by implementing the appropriate processes, Access Control Lists, Encryption, and Threat detection.
Security Measures in SIX ERP:
- Access Control Lists
- User Roles
- Two Factor Authentication (TFA)
- Encryption
- SSL
- Pod Isolation
- Threat and Intrusion detection

Access Control Lists (ACLs) are a security feature used in Enterprise Resource Planning (ERP) systems to control which users can access data. ACLs work by assigning permissions to users or groups of users, specifying which actions they are allowed to take on which data. This will enable administrators to control who can see and edit specific data within the system.
ACLs are typically implemented as a list of permissions associated with each user or group. These permissions might include read, write, and delete privileges or other actions required for the system. When a user attempts to access data, the ACL is checked to determine whether they have the appropriate permissions to do so. If they do not, the request is denied.
ACLs can be configured in SIX ERP in a few different ways. The most common approach is to use role-based security, where users are assigned to roles, and the roles are then granted the appropriate permissions. This approach is popular because it is easy to configure and manage. Another method is to use object-based security, where each object in the system has its very own ACL. Object-Based ACLs can be more complex to set up but offers added flexibility, especially for staff across departments.
ACLs are an essential part of the SIX security strategy. ACLs help ensures that only authorized users can access sensitive data and help protect your organization's data from unauthorized access or modification.
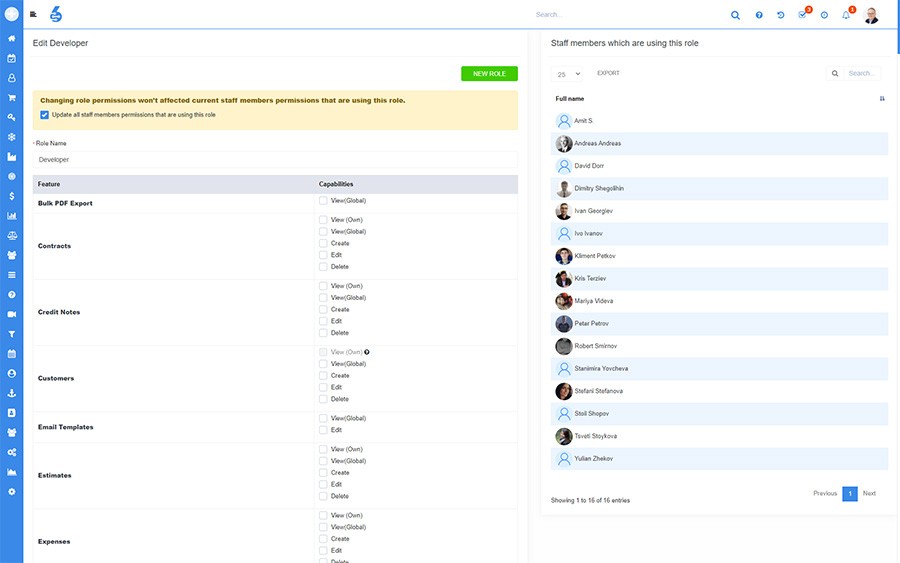
There are a few roles that are pre-defined in SIX ERP. Each of those roles has a specific purpose. The roles help protect the system and ensure people can't do things they're not supposed to. Administrators, Super Administrators, and simple Staff roles are examples of pre-defined roles. Depending on the use case, Administrators enhance the system by defining additional roles, e.g., Sales Staff, Project Manager roles, or Warehouse Worker roles.
Two Factor Authentication (2FA) is a process that helps to protect your account by requiring two forms of identification before allowing login. The most common way to provide 2FA is via a combination of something you know, such as a password, and something you have, such as a security key or code. After providing your username and password when you try to log in, you will also be asked to provide the security key or code. This extra layer of security can help to protect your account from unauthorized access, even if someone knows your password.
In SIX ERP, 2FA is used to protect user accounts, data, and systems. For example, after providing your username and password, you may be asked to provide a security code generated by the system and sent via text message or email. This code can then be entered into the system to verify your identity and allow access. 2FA can also be used to help protect data stored in the system.
One of the most critical aspects of SIX ERP security is ensuring that sensitive data is encrypted. This helps to ensure that if any of this data is compromised, it can't be accessed and used maliciously. Several different encryption algorithms are used, depending on the specific needs or function.
SIX ERP uses algorithm-based encryption interchange between AES (Advanced Encryption Standard) 2048 and RSA (Rivest Shamir Adleman).
The Transport Layer Security (TLS) protocol provides a mechanism for secure communications over a computer network. TLS is the most current and widely used version of the SSL protocol. TLS uses a combination of symmetric-key cryptography and public-key cryptography to secure communications.
TLS provides two primary security services:
- Confidentiality - Data is encrypted, so the intended recipient can only read it.
- Authentication - The identity of the sender or receiver is verified, ensuring that the data has not been tampered with in transit.
TLS is widely used on the Internet, including in web browsers and email applications. TLS is also used in corporate networks for secure communications between computers and servers. SIX ERP uses SSL/TLS encryption for all in-transit information from our infrastructure to yours - and vice versa.
By isolating your ERP system in its secure POD, SIX keeps your data safe and prevents costly breaches. Contrary to the SAAS systems, a high level of Data Isolation is key to keeping neighbors out and your data secured and contained. POD isolation is the key to keeping your data safe.
Threat and intrusion detection are integral to the SIX ERP security management plan. We help organizations protect their data and systems from harm by monitoring for and identifying threats and intrusions. Many different techniques are used for threat and intrusion detection, including:
- Pattern recognition: Identifying unusual patterns in system activity.
- Vulnerability scanning: Scanning SIX ERP systems for known vulnerabilities.
- Penetration testing: Conducting simulated attacks on systems to identify weaknesses that real attackers could exploit.
We carefully consider the threat and intrusion detection methods most appropriate for our client's security.
“ The most customizable solution we found replacing our legacy CRM solution we worked with for too long. ”

Ludomil Lakov
Director of Sales | CANTEKWant to see SIX for yourself?
Need help, have questions or want to get a free demo?
Please read our Privacy Policy on how we process personal data. We will never share your data!